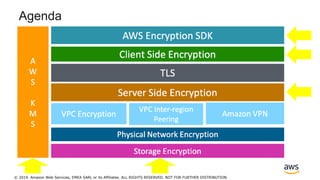
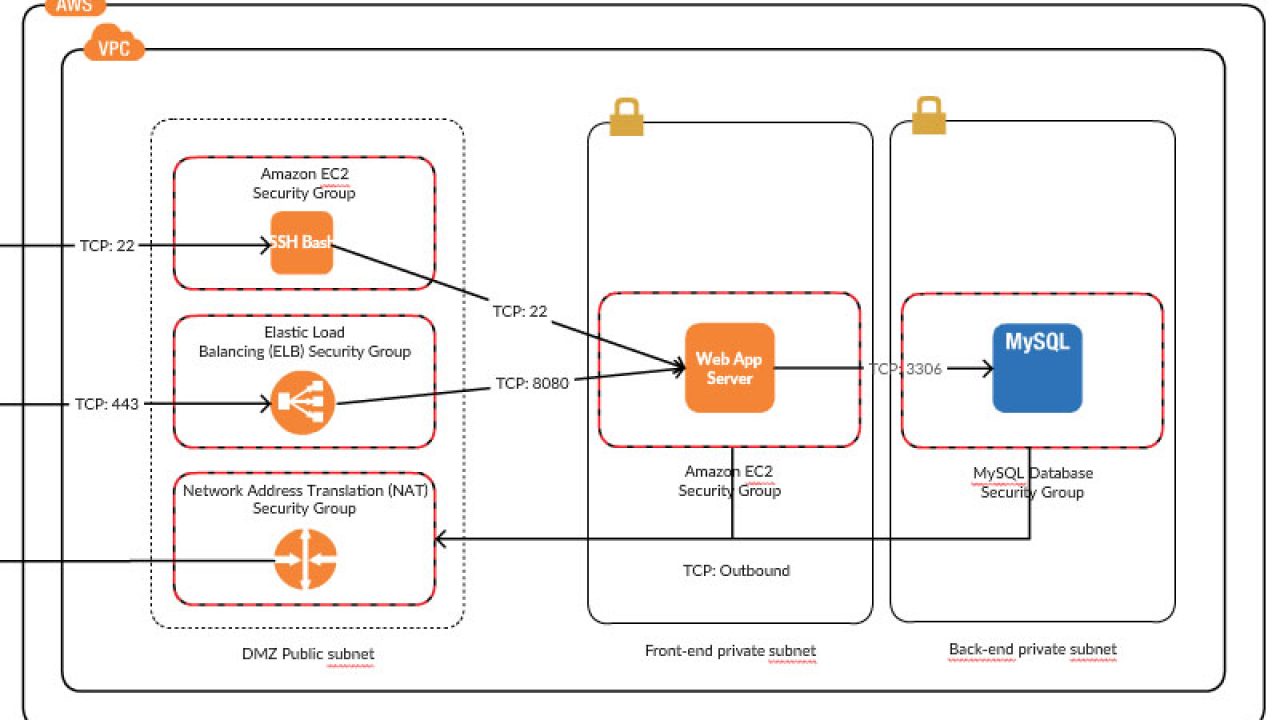
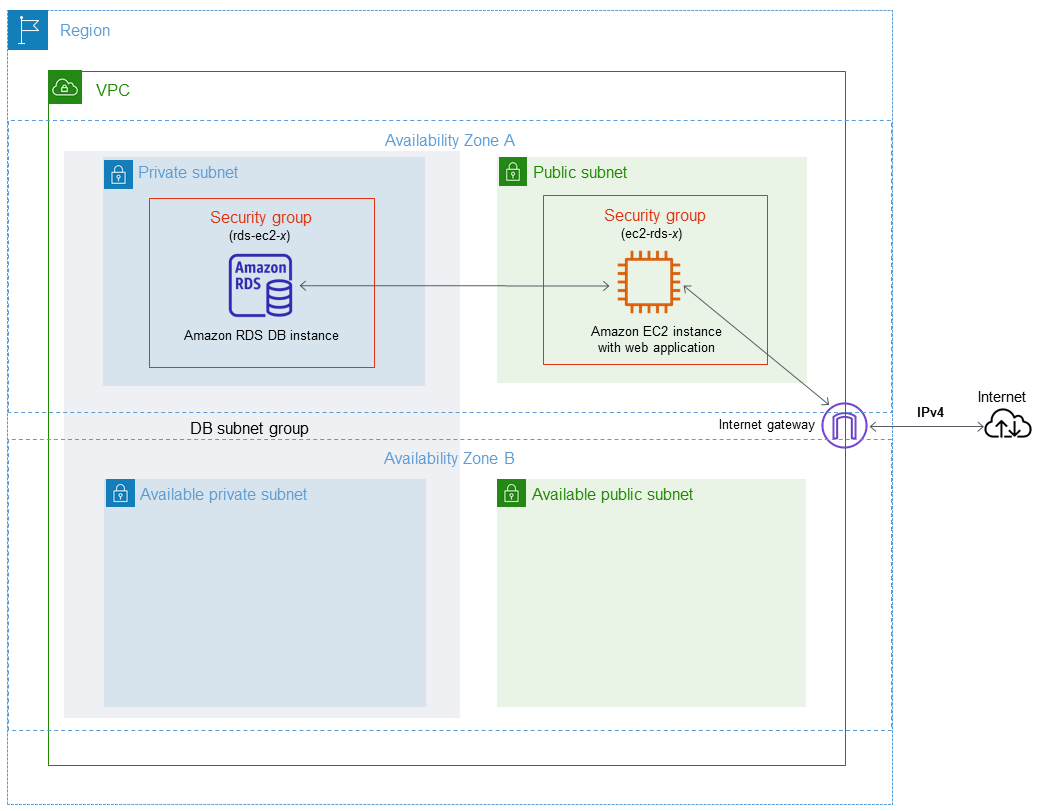
How to Migrate Amazon EC2 Instances from EC2-Classic to Amazon VPC with CloudEndure | AWS Partner Network (APN) Blog

How to set up an outbound VPC proxy with domain whitelisting and content filtering | AWS Security Blog

Implementing security notifications for end user activity on Amazon FSx for Windows File Server | Windows on AWS