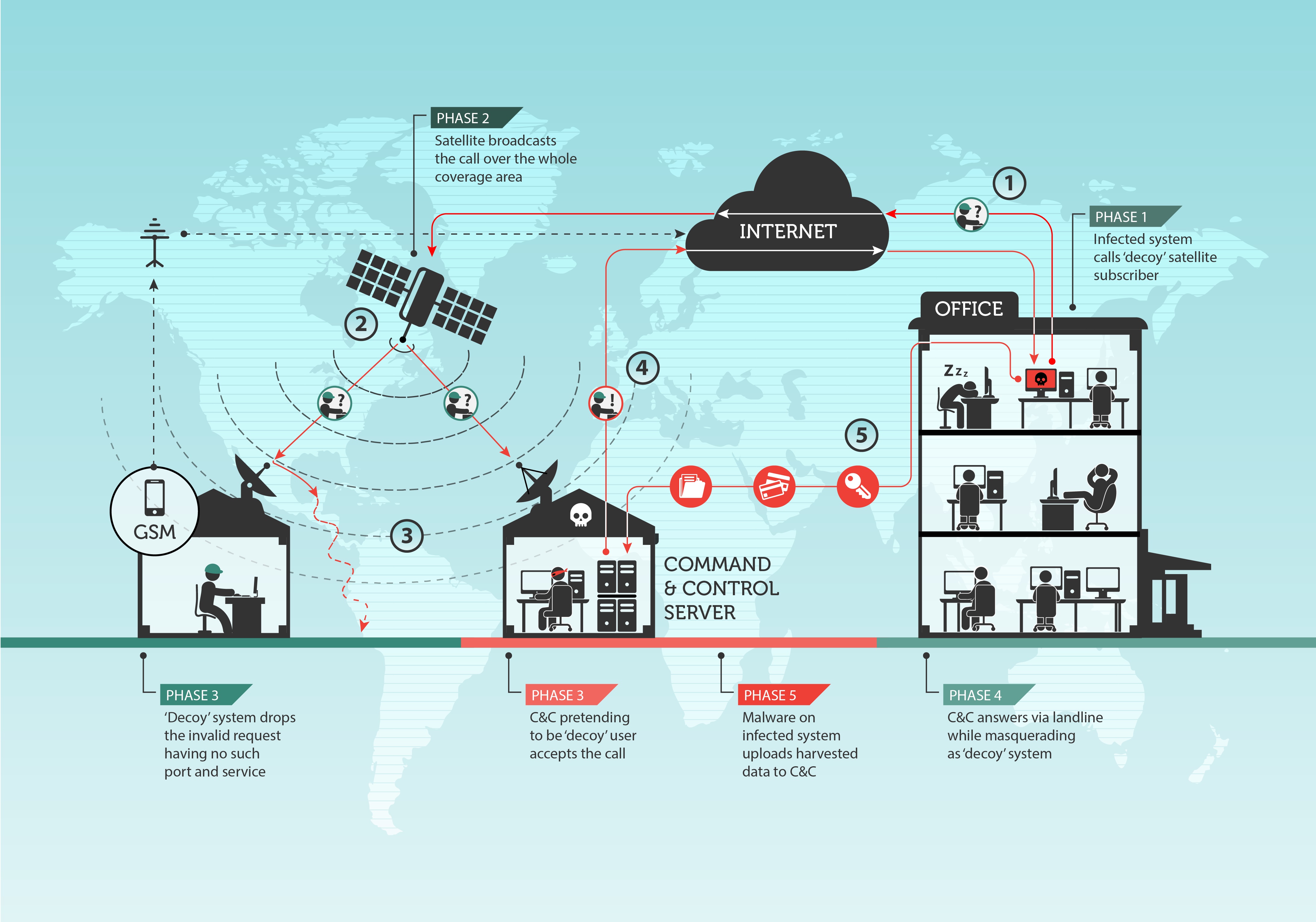
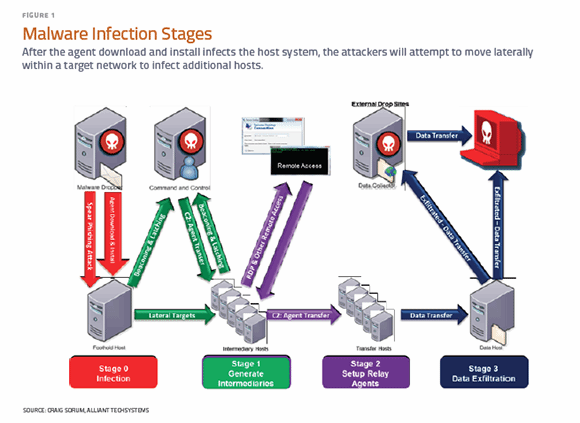
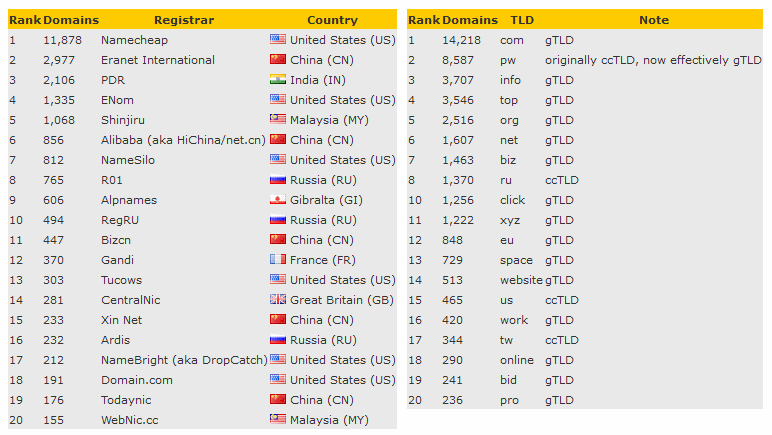
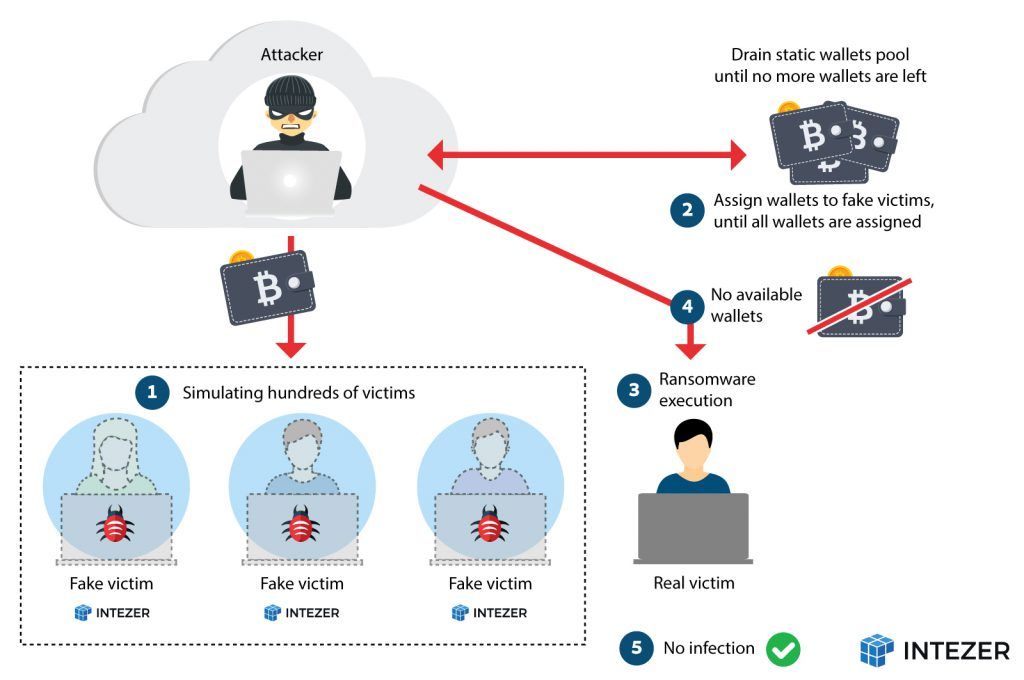
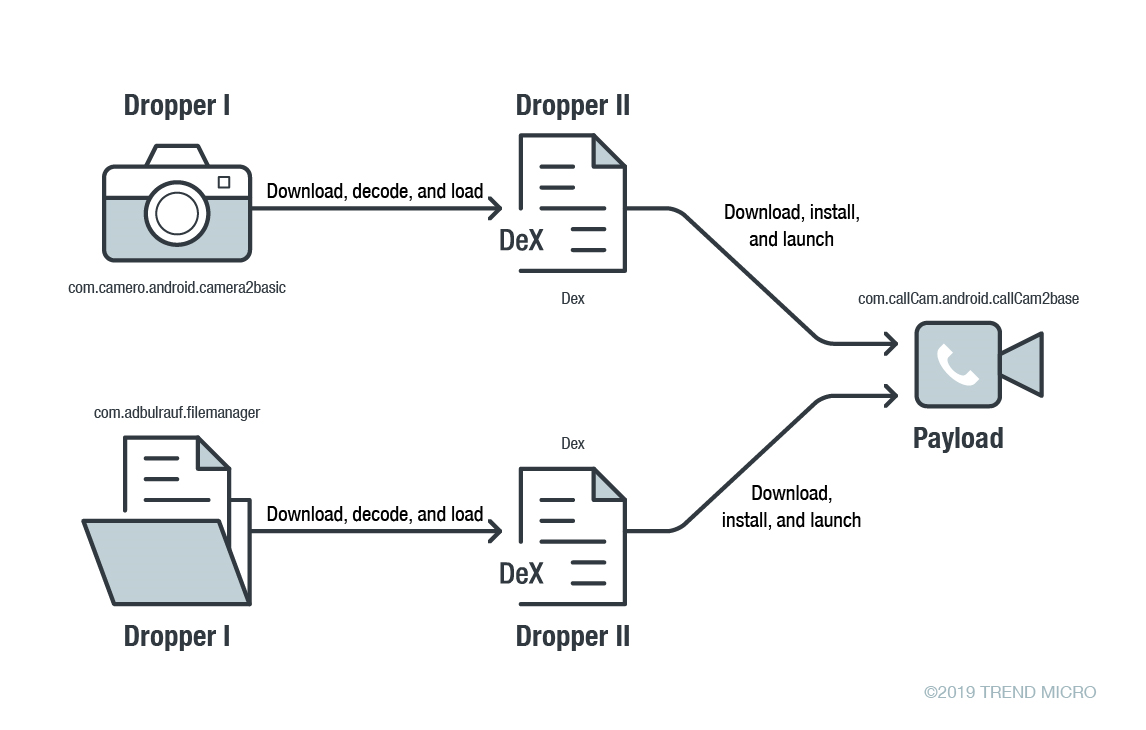
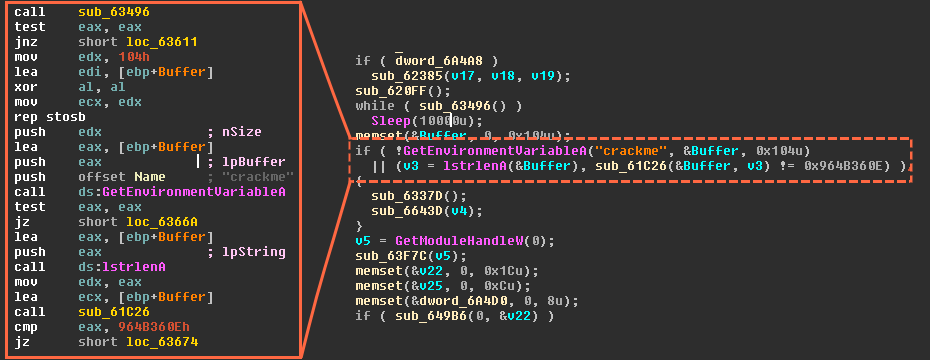
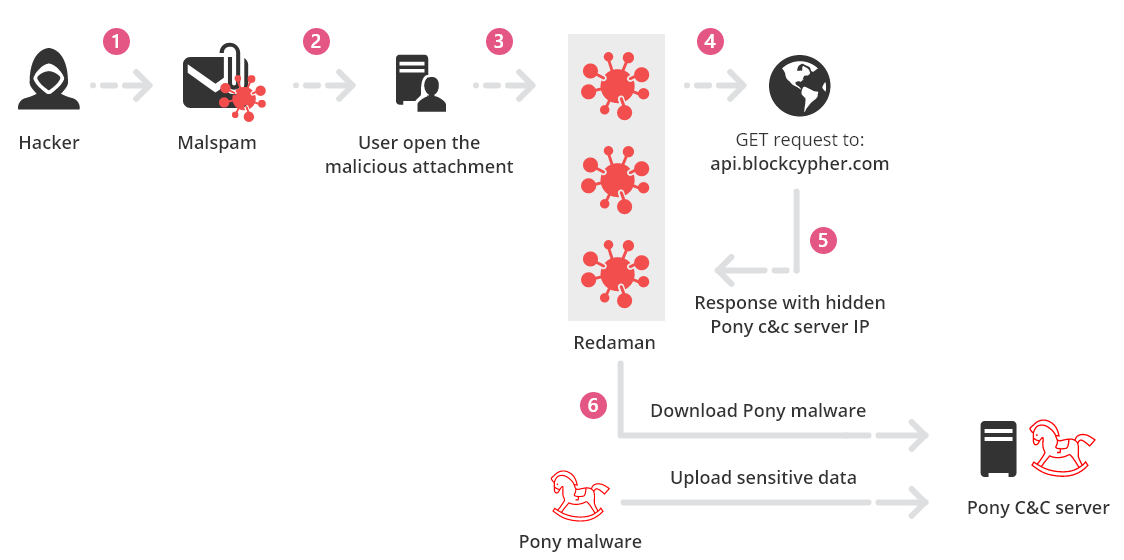
Glupteba Campaign Hits Network Routers and Updates C&C Servers with Data from Bitcoin Transactions - ThreatRavens

ESET research on Twitter: "#Evilnum uses several malicious components in its attacks. Each operates independently and has its own dedicated C&C server. The JS backdoor initially compromises the system and other components